

4.2. Live Guard
SpyEraser Live Guard is a real time built in protection feature that protects your computer by checking files for suspicious spyware as they are opened. Live Guard scans all starting applications and alerts you as to what it finds.
Real Time Protection (Security Monitors) Settings
Real Time Protection increases system security by defending your system from spyware attacks and eliminating them. Real-time spyware threat protection extends the level of Security Guards protection. It enhances your safety by not only detecting downloads of spyware to your system but also preventing the changes that can be done to your system. Check the box Enable the Security Guards (Recommended) to activate this option.
After enabling or disabling any of the settings, click on the Apply button on the screen for the changes to take effect. To apply the default settings, click on the Default button and then click Apply button to apply the default settings.
Appropriate action from additional options
These are:
To access this section, choose the option Application Guards placed in the left menu of the Live Guard window. Through this section, you can monitor running applications.
Installed Components
It keeps a check if additions are made to the installed component list.
It monitors changes in the list of registered programs or applications installed on your computer.
Application Restrictions
It restricts illegal intrusions and alterations to the applications restriction policies.
This option forbids the user from running certain Windows programs by setting RestrictRun option in the registry.
Internet Explorer Menu Extensions
It restricts unauthorized changes that can be made to Menu Extensions in Internet Explorer.
The items in Context Menu of Internet Explorer are called Internet Explorer Menu Extensions. These menu items are available when right-clicking a web page in a browser.
Process Execution
It prevents the spyware programs downloaded to your system from execution.
The security monitors running on your computer will prompt you to allow or block the execution of an unknown program when it runs for the first time. Thus, if a spyware or a malicious program is installed, you can enhance security by removing such programs on receiving any warning.
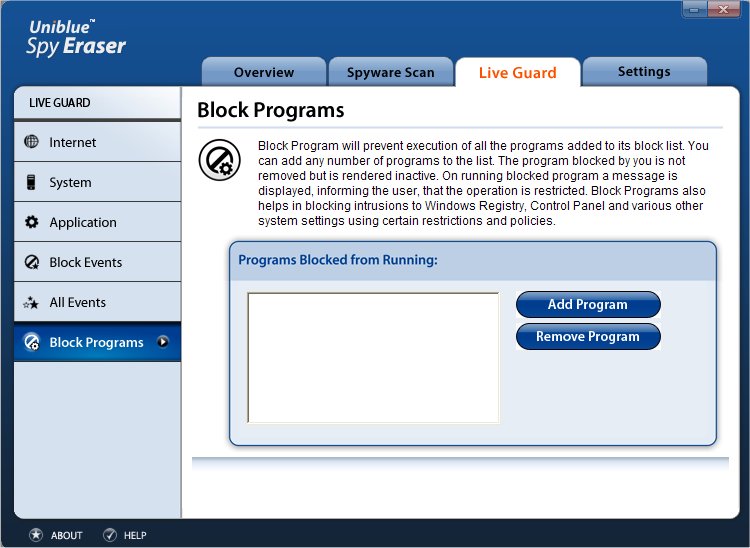
Block Events
SpyEraser has an in-built real-time monitoring system that can prohibit an unknown program from executing on your system. When an unknown program self executes, an alert message prompts you to either allow or block the execution of the program. All the programs blocked through this channel are displayed in the Block Events window. This window provides details about Total Items blocked along with their Date, Time, Type and Description.
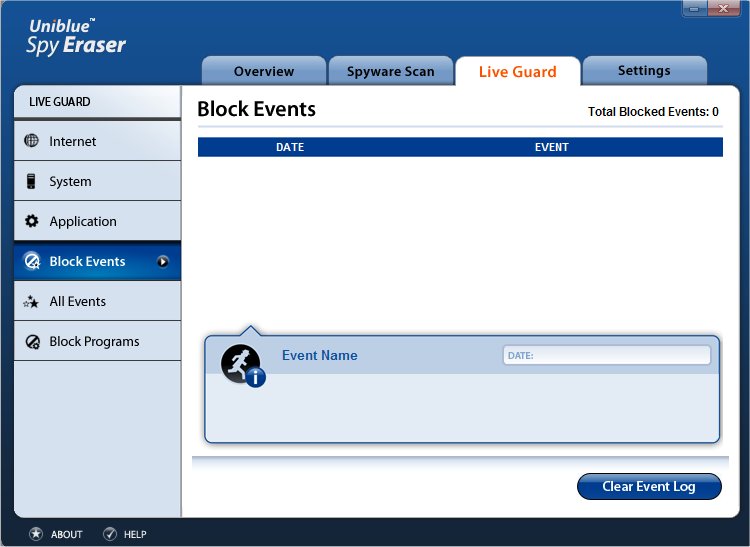
On selecting an item, you can view its additional details in the supplementary details section. If you want to delete all the logs of the Blocked Events, click on the Clear Event Log button.
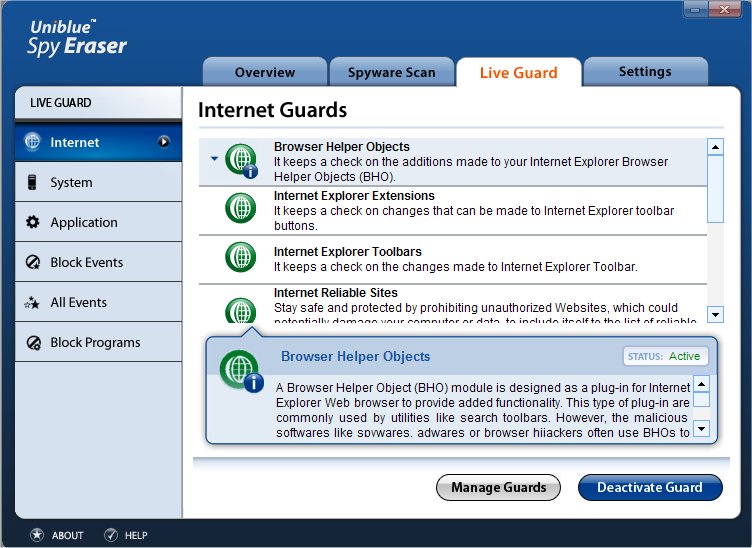
Internet Guards
To access this section, click the option Internet Guards placed in the left menu of the Live Guard window. Through this section, you can set security checks for all Internet based malware.
Browser Helper Objects
It keeps a check on the additions made to your Internet Explorer Browser Helper Objects (BHO).
A Browser Helper Object (BHO) module is designed as a plug-in for Internet Explorer Web browser to provide added functionality. This type of plug-in is commonly used by utilities like search toolbars. However, malicious software like spyware, adware or browser hijackers often use BHOs to pop-up advertisements or study your browsing pattern because a BHO has access to each URL you visit and can redirect you to unwanted websites or display other pages than you requested.
Internet Explorer Extensions
It keeps a check on changes that can be made to Internet Explorer toolbar buttons.
Internet Explorer toolbar buttons or the items placed in the Tools menu of Internet Explorer which are not included in the default installation are controlled by Internet Explorer Extensions. The toolbar button functions to run an application, a script, or open an Explorer Bar.
Internet Explorer Toolbars
It keeps a check on the changes made to Internet Explorer Toolbar.
A horizontal strip of buttons docked under the Menu Bar in Internet Explorer which provides shortcut for commonly used commands is a Toolbar.
Internet Reliable Sites
This option will help you stay safe and protected by keeping away unauthorized websites from being added to the list of reliable websites. Reliable websites are genuine and do not exploit the data stored on your computer.
Internet Explorer Restrictions
It restricts illegitimate changes that can be made to the Internet Explorer Restrictions policy setting.
Using Internet Explorer Restrictions policy, the administrator can prohibit the users from changing certain settings in Internet Explorer, for example, setting a new homepage. Although, spyware can also use this policy restriction and prohibit user from making changes to their own computer.
Internet Explorer Trusted Sites
It restricts unwanted sites from being added to your list of Trusted Sites.
In Trusted Sites Zone, the content of Web sites is considered more reputable or trustworthy than other sites on the Internet. Users can use this zone to assign a higher trust level to these sites to minimize the number of authentication requests.
Internet Explorer Explorer Bars
It restricts illegitimate changes to standard protocol drivers.
The exchange of information to and from your computer is accessed by some spyware. This is done using the Windows protocols filters and handlers.
Internet Explorer ShellBrowser
It restricts changes that can be made to the Internet Explorer Shell.
Information and settings about an instance of Internet Explorer are contained in Internet Explorer ShellBrowser. Modifying these settings or adding new ShellBrowser can take control of Internet Explorer and add toolbars, menus, and buttons.
Internet Explorer URLs
It keeps a check on the predefined URLs in Internet Explorer to prevent browser hijacking or any other changes that can be made to your Internet Explorer browser.
Internet Explorer Web browser
It prohibits any changes that can be made to Internet Explorer Web browser.
Information and settings about an instance of Internet Explorer are contained in Internet Explorer Web browser. Modifying these settings or adding a new Web browser can take control of Internet Explorer and add toolbars, menus, and buttons etc to it.
URL Search Hooks
It restricts illegitimate changes that can be made to Internet Explorer URL Search Hooks. URL Search hooks are used by Internet Explorer to translate the address of an unknown URL protocol.
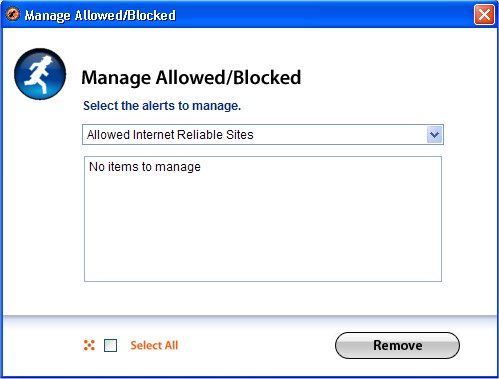
Note: By default, the status of the guards is always active. To disable them, select the guard from the Application Guards section and click on Deactivate This Guard option. It provides the Status and Description of the guard. Additionally, you can maintain a list of allowed and blocked options or view the same list by clicking the Manage Allowed / Blocked link. Clicking on the option will open a new window where you can manage the relevant options.
![]()
Copyright (c) 2006 Uniblue Systems Ltd. All rights reserved.